OIT is deploying a risk-based verified push feature in Duo that will help cut down on compromised accounts and improve cybersecurity all across campus.
What is a DUO Verified Push? Examples Below
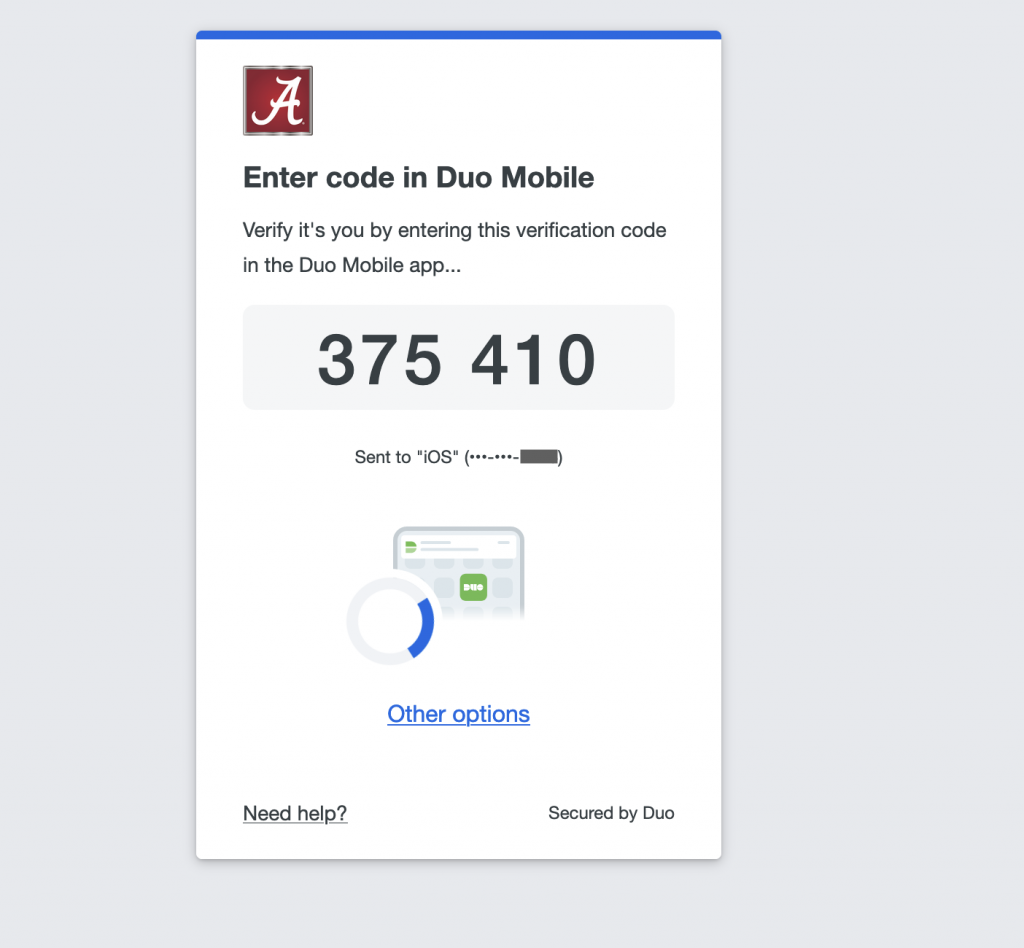
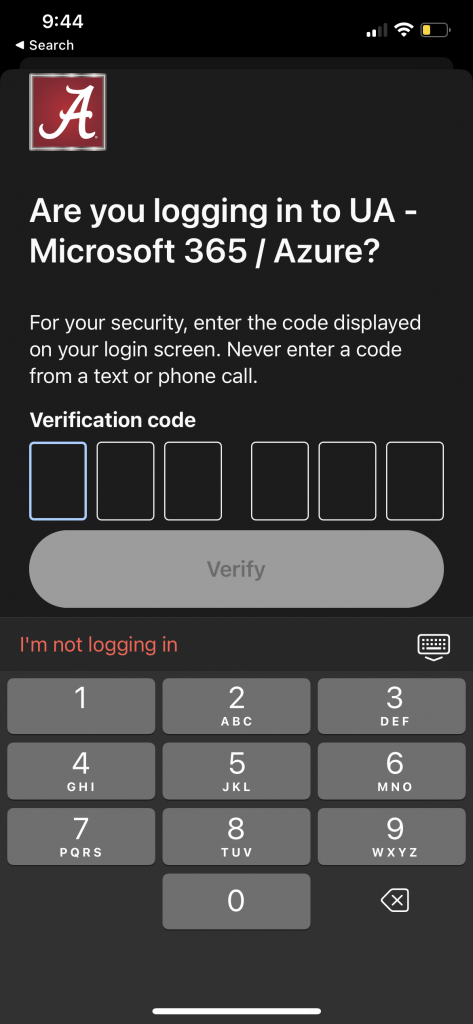
Verified Push is a more secure version of Duo Push that requires users to enter a numeric code from the authentication prompt on their mobile device. When Duo detects an anomaly in your login pattern, it will display a code on the screen the person is using to log in. You will simultaneously get a request to answer the code in your Duo app. The code will be a mandatory step to log in the first time you use the device, but will happen less frequently the more you use the device.
Duo’s Risk-Based Authentication automatically detects and mitigates commonly known attack patterns and high-risk anomalies. Risk-Based Authentication consists of two key capabilities: Risk-Based Factor Selection and Risk-Based Remembered Devices.
How is risk assessed by DUO?
- User marked fraud: A user has indicated they weren’t responsible for a login by marking it as suspicious in the Duo Mobile app.
- Push harassment: A pattern of failed authentications is consistent with an adversary performing a targeted push harassment attack against a single user.
- Push spray: A pattern of failed authentications is consistent with an adversary performing a non-targeted push attack against multiple users.
- Unrealistic travel: A user attempts to authenticate from a new location that would be impossible to reach based on the past authentication time and location.
- Country code mismatch: The authentication device and access device appear to be in two different countries.
- Novel ASN: A user attempts to authenticate from an autonomous system number (ASN) not seen in the organization’s recent history of successful authentication.
What is the point?
Verified Duo Push automatically adds a separate layer of security on top of the push by asking the user to complete an action that requires them to interact with both the access and the authentication devices.
Limitations
- Apple Watch experience is degraded. The full QWERTY keyboard makes entering the code a challenge. You are able to illustrate or narrate your code as an alternative.
- In iOS, the numeric keyboard is only launched in the Duo app. If you attempt to approve directly from notification, you will have QWERTY. The approval still works, just less smoothly.
- Verified Push only works when combined with the Duo mobile app. Phone call and SMS authentication are unsupported. Hardware token usage is unchanged as well. If a phone call is the only way to authenticate due to accessibility reasons, we can add the user to an exception group.
Want to learn more?
You can find out more about Verified Push on Duo’s website: CLICK HERE